Smart DIH - Security
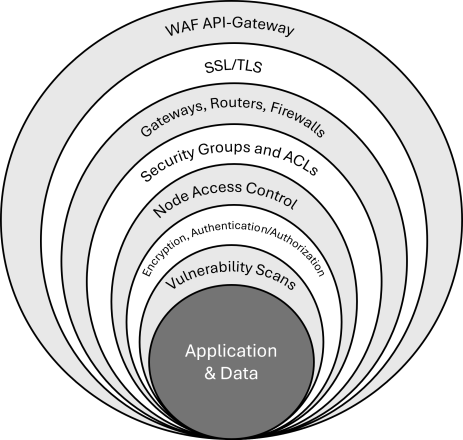
The Smart DIH![]() Smart DIH allows enterprises to develop and deploy digital services in an agile manner, without disturbing core business applications. This is achieved by creating an event-driven, highly performing, efficient and available replica of the data from multiple systems and applications, security controls for application and data can be illustrated by the following seven layers:
Smart DIH allows enterprises to develop and deploy digital services in an agile manner, without disturbing core business applications. This is achieved by creating an event-driven, highly performing, efficient and available replica of the data from multiple systems and applications, security controls for application and data can be illustrated by the following seven layers:
-
Vulnerability Scans
-
The components in the platform are constantly tested against the CVE database.
-
Docker images that are used are also checked for CVEs.
-
-
Encryption, Authorization and Authentication
-
The data in the data-grid can be encrypted.
-
Data in Kafka
 Apache Kafka is a distributed event store and stream-processing platform. Apache Kafka is a distributed publish-subscribe messaging system.
A message is any kind of information that is sent from a producer (application that sends the messages) to a consumer (application that receives the messages).
Producers write their messages or data to Kafka topics. These topics are divided into partitions that function like logs.
Each message is written to a partition and has a unique offset, or identifier. Consumers can specify a particular offset point where they can begin to read messages. is encrypted using volume encryption provided by the underlying blob store.
Apache Kafka is a distributed event store and stream-processing platform. Apache Kafka is a distributed publish-subscribe messaging system.
A message is any kind of information that is sent from a producer (application that sends the messages) to a consumer (application that receives the messages).
Producers write their messages or data to Kafka topics. These topics are divided into partitions that function like logs.
Each message is written to a partition and has a unique offset, or identifier. Consumers can specify a particular offset point where they can begin to read messages. is encrypted using volume encryption provided by the underlying blob store. -
Access to data in the data-grid is provided only to trusted users (see IDP
 An identity provider, or IDP, stores and manages users' digital identities. IDP and SSO can work together to authenticate users. and Oauth2 sections).
An identity provider, or IDP, stores and manages users' digital identities. IDP and SSO can work together to authenticate users. and Oauth2 sections). -
RBAC
 Role-based access control (RBAC), also known as role-based security, is a mechanism that restricts system access. It involves setting permissions and privileges to enable access to authorized users. rules are defined for data-grid access by the data entity (see Roles and Privileges section).
Role-based access control (RBAC), also known as role-based security, is a mechanism that restricts system access. It involves setting permissions and privileges to enable access to authorized users. rules are defined for data-grid access by the data entity (see Roles and Privileges section).
-
-
Node Access Control
-
Processes in the nodes run in dockers where access is limited to docker entities by enforcing specific user:group access.
-
-
Security Groups & ACLs - Cloud Private Network Security
-
All nodes are running within the private network.
-
Opening security groups to specific ports and entities (gateways load-balancers).
-
-
Gateway, Routers, Firewalls
-
Gateways are setup for VPN access to avoid any other connectivity.
-
Routers have routing
 The mechanism that is in charge of routing the objects into and out of the corresponding partitions. The routing is based on a designated attribute inside the objects that are written to the Space, called the Routing Index. roles specific to the topology.
The mechanism that is in charge of routing the objects into and out of the corresponding partitions. The routing is based on a designated attribute inside the objects that are written to the Space, called the Routing Index. roles specific to the topology.
-
-
-
Communication to and from the platform is performed in TLS (TLS 1.2).
-
-
WAF API-Gateway
-
For services that are exposed to external users (intranet or internet) an API Gateway is added. The API Gateway authorizes the service request (accessing the servicing part of the platform).
-
WAF is optional and added mainly in zero-trust cases where additional rules are applied.
-
IDP Integration
GigaSpaces supports integration with identity providers (IDP) which support OpenId Connect protocol like Okta and Azure AD. Users or SpaceDeck![]() GigaSpaces intuitive, streamlined user interface to set up, manage and control their environment. Using SpaceDeck, users can define the tools to bring legacy System of Record (SoR) databases into the in-memory data grid that is the core of the GigaSpaces system. (platform control and monitoring) are managed via the IDP and user groups in the IDP are mapped to roles.
GigaSpaces intuitive, streamlined user interface to set up, manage and control their environment. Using SpaceDeck, users can define the tools to bring legacy System of Record (SoR) databases into the in-memory data grid that is the core of the GigaSpaces system. (platform control and monitoring) are managed via the IDP and user groups in the IDP are mapped to roles.
For IDP setup details refer to our SpaceDeck - SSO IDP Setup page found in our User Guide
Roles & Privileges
User and service accounts can be assigned to roles which limit their access to the data-grid and platform control. A role is a collection of privileges, each defines an allowed operation for a resource. Some privileges are system level and some are associated to specific resources which are either a data-grid level, a Space![]() Where GigaSpaces data is stored. It is the logical cache that holds data objects in memory and might also hold them in layered in tiering. Data is hosted from multiple SoRs, consolidated as a unified data model. or a table.
Where GigaSpaces data is stored. It is the logical cache that holds data objects in memory and might also hold them in layered in tiering. Data is hosted from multiple SoRs, consolidated as a unified data model. or a table.
For details about Roles & Privileges refer to the our Security Overview page found in our Architectural Overview section.
Auditing
Each operation performed by SpaceDeck (pipelines, services, data-grid/Spaces) is audited and can be found in a log containing both the user ID and the operation performed. The IDP logs user logins and logouts.
For information about Smart DIH![]() Digital Integration Hub.
An application architecture that decouples digital applications from the systems of record, and aggregates operational data into a low-latency data fabric. refer back to the Smart DIH contents page and choose another topic.
Digital Integration Hub.
An application architecture that decouples digital applications from the systems of record, and aggregates operational data into a low-latency data fabric. refer back to the Smart DIH contents page and choose another topic.
 In-Memory Data Grid - achieve unparalleled speed, persistence, and accuracy.
In-Memory Data Grid - achieve unparalleled speed, persistence, and accuracy.